Today’s world is defined by data, and for many businesses, it is one of the most highly valued assets. At enterprise scale, vast amounts of sensitive data are at rest and in motion in what are, quite often, complex IT architectures.
This makes them prime targets for cybercriminals, exploiting loopholes in security for network intrusion, often with the intent of stealing data. Quite simply, protecting sensitive information is paramount for businesses of all sizes. To manage these risks effectively, enterprises observe stringent information security protocols.
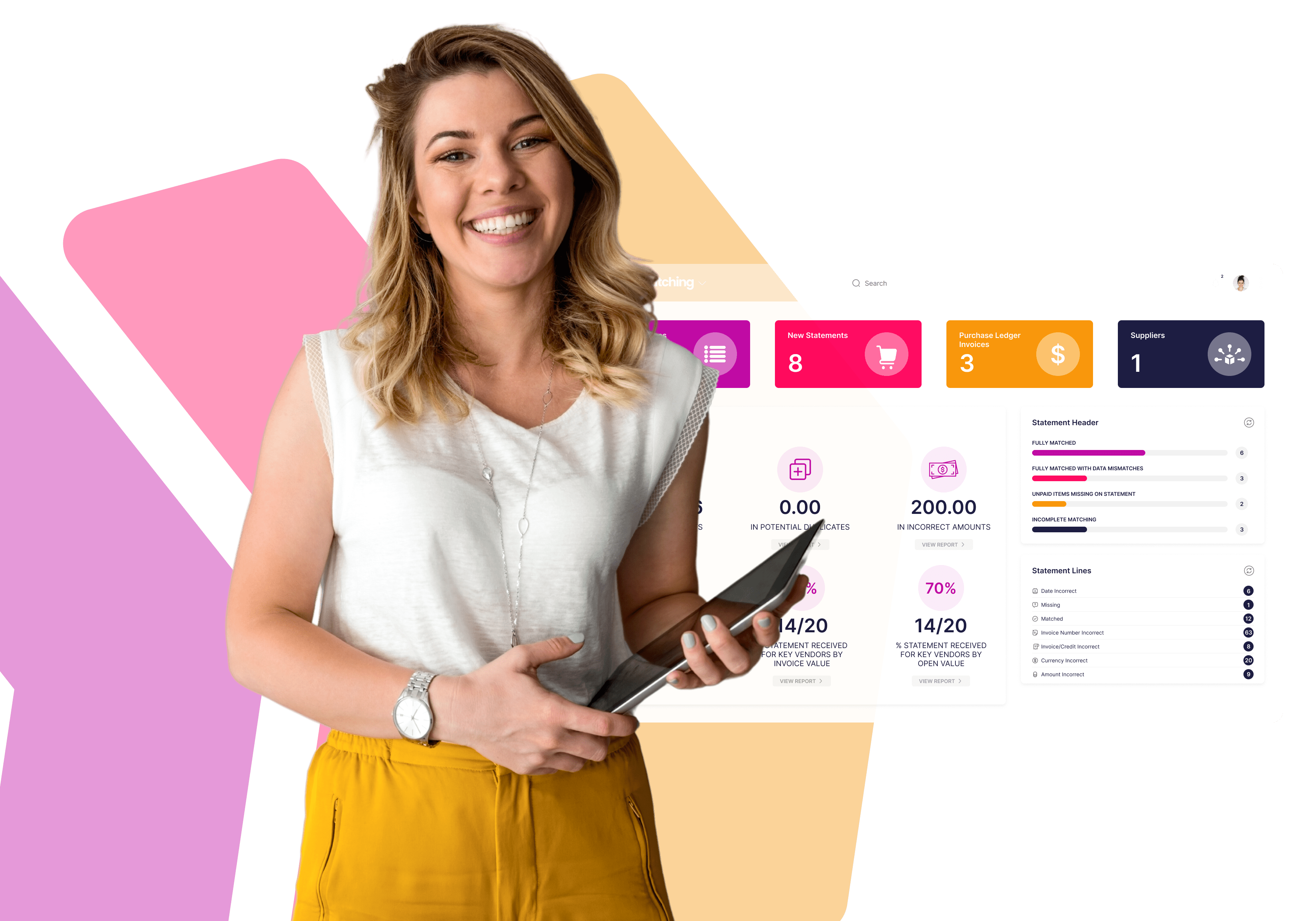
APMatching is committed to providing secure and reliable SaaS solutions to enterprise customers worldwide. We’ve always implemented stringent InfoSec processes as part of our onboarding procedures, ensuring that our client’s data remains protected from the moment they join our ecosystem.
As we have grown, we have developed our software and services to close the loop in AP automation by combining invoice matching, ledger verification and duplicate invoice detection. In parallel with this, we have also evolved our security posture.
As part of our commitment to delivering solutions that fully meet the needs of global enterprises, we embarked on a journey to achieve world-class standards for information security. We’re proud to announce that we have now successfully obtained ISO 27001 certification, a globally recognized information security management system (ISMS).
Our pursuit of excellence in information security extends beyond ISO 27001. We’ve also adopted other essential frameworks to safeguard our clients’ data and ensure compliance with IT industry regulations.
Our software and services are hosted on the Microsoft Azure cloud, leveraging its robust infrastructure and security features. We’ve implemented a single-tenant architecture, ensuring that each customer gets their own isolated instance, enhancing resilience and security.
Azure’s global network of data centers provides us with the flexibility to host our client’s data in the region that best suits their needs: North America, EU, UK, or APAC. This minimizes latency by ensuring that data residency is optimized for where it’s being used, and that data sovereignty fits with compliance and local data privacy regulations, such as GDPR.
To further enhance our security posture, we leverage Windows Defender for the Cloud, a comprehensive cloud security solution that dynamically manages our environments per ISO 27001:2013 and SOC 2 regulatory frameworks.
This provides a comprehensive approach to security by virtue of adopting a cloud-native application protection strategy. Real-time vulnerability scanning, monitoring and assessment are central to maintaining vigilance against threats.
In addition to ISO 27001, we adhere to the Cyber Essentials security framework, the UK government-endorsed standard designed to ensure minimum levels of threat management through annual assessment and certification. This framework focuses on five technical areas of cybersecurity: Network boundaries, secure configuration, access control, malware protection, and patch management.
Through our continuing accreditation to Cyber Essentials, we demonstrate our commitment to safeguarding our client’s data against common cyber threats. The latest updates to the framework, including cloud services and multi-factor authentication, further reinforce our commitment to keeping pace with evolving cybersecurity requirements.
While ISO 27001 and Cyber Essentials are widely recognized standards, different territories place varying emphasis on different information security frameworks. For enterprises domiciled in the United States, the SOC 2 framework is particularly relevant.
Recognizing this, we maintain compliance under the SOC 2 framework, ensuring that our security practices meet the specific requirements of US businesses. This framework focuses on five trust service principles: Security, availability, confidentiality, processing integrity, and privacy.
In meeting SOC 2 compliance, our US-based customers can be sure that we fully understand the specific regulatory requirements of US-domiciled enterprises and that our platform and software fully support their security architectures.
The first step to adopting the invoice automation solution that protects your enterprise data with world-class security isn’t complicated.
Take a personalised demo with one of our representatives, and we’ll show you how the software eliminates tedious, time-consuming manual invoice processing and automates duplicate invoice detection.
If you like what you see, we’ll give you full support so that you can more fully evaluate APMatching with a Proof of Concept (PoC), demonstrating how effective it is using your own data.
Book a live demo to see the end-to-end processes on live customers systems and learn how easy it is to try this for free on a Proof of Concept.
Book a Live Demo to see the end-to-end processes on live customers systems and learn how easy it is to try this for free on a Proof of Concept.